- ... architectures1.1
- To handle different byte ordering schemes and the differences
between
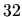 and
and 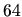 bit CPUs.
bit CPUs.
- ... suite1.2
- The former TMA suite
- ...2.1
- Depending on the runtime environment (dynamic linker, libraries)
dynamic instantiation is directly performed via the dl interface (dlopen) or via a programmatic construct (switch). In the latter case the
instantiation is not really dynamic in the narrow sense, because all possible
implementations must be known at compile time. The mechanism is, however,
transparent to the application.
- ... problem2.2
- The choice of which algorithm is used strongly depends on the absolute
number of point locations that are performed during the simulation. For few point locations
the preprocessing time that is necessary to build the oct-tree will be
dominating, whereas for a relatively large number of point locations the search time
will be the limiting factor.
- ... database3.1
- The actual location (file or database) of the data is transparent.
- ...
values3.2
- Concrete values (e.g. double, string, ...) are derived
from the abstract value interface. Therefore, any data type of the used
programming language (C++) can be used as a value.
- ... code3.3
- If the constructor is used then the include
file that contains the definition of this Reader implementation must be
included in the application program.
- ... attribute3.4
- The actual differences are hidden by the use of
interfaces.
- ... handle3.5
- The WAFER-STATE-SERVER uses a simple garbage collection mechanism
(handles) to avoid memory leaks. A 0 assignment to an instance of a handle
class results in a call of the destructor on that object if there was exactly
one handle to the object. Please refer to Section 3.7.1 for a
description of the handle class.
- ... ignored3.6
- Note
that a mixture of different spatial dimensions in one
file is neither useful nor legal. It was nevertheless decided to issue only a
warning instead of a fatal error as this helps in detecting several such errors
at once as opposed to only one error per Reader invocation. This is useful
when WSS files are generated by hand.
- ... managed3.7
- While the time spent in the reading process of a three-dimensional
simulation run is negligible, it certainly does matter for visualization. This
is even more relevant if not one but many simulation results are stored and are
to be viewed from a browser-like program.
- ...
address3.8
- Multiuser and multitasking operating systems need to manage
additional information such as the user and process IDs the memory region
belongs to.
- ...
omitted3.9
- This information is determined at compile time; the overhead is
totally eliminated.
- ... time4.1
- The programming language FORTRAN77 does not
offer a standardized, platform independent, dynamic memory allocation
mechanism.
- ...
conforming4.2
- This can be the case if the Wafer was already generated
with interface conforming grids in a previously performed simulation.
- ... triangles4.3
- The etch front is represented by refined cells only.
The triangulation of the etch front takes place by splitting the interface
between material and vacuum into two equal sized triangles.
- ... questionable5.1
- If the simulation
failure occurs during the computation of the gradient, the step direction will
be computed incorrectly
- ...5.2
- On
WINDOWS machines all jobs will have the same nice level, thus the regular
rank
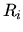 is used.
is used.
- ... ignored5.3
- They are realized as comments.
- ... two5.4
- A crossover with two parents is called a sexual crossover
operation. This mimics a biological reproduction mechanism. There are, however,
also algorithms that combine three or more individuals (asexual crossover).
- ... number5.5
- In the inverse modeling example that is presented in
Section 5.6 an analytical model to approximate the dopant profile of a
transistor is used, where the genes directly correspond to the parameters of the
model.
- ... optimizer5.6
- The programs use
the standard input and standard output channels that are associated with every
UNIX program or WINDOWS console application.
- ... clusters5.7
- The ratio
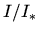 is called interstitial
supersaturation.
is called interstitial
supersaturation.
- ... grids7.1
- The grids
of a Wafer need not be boundary conforming.
- ...7.2
- Note
that in this case the smallest possible grid that is necessary to represent the
geometry should be used to minimize the overhead that is introduced by
representing a segment without any quantities via the hull of a grid.